As eventful as 2020 has been, cybersecurity has managed to stay in the headlines. In October alone, the US government’s Cybersecurity and Infrastructure Security Agency issued the equivalent of one alert per day for industries and businesses, and the head of the Securities and Exchange Commission warned corporations needed to boost vigilance against a possible wave of attacks.
The good news is that many businesses are paying attention. Cybersecurity awareness has grown by leaps and bounds, with one recent survey finding almost 80% of businesses rank cybersecurity among their top five concerns, up from just over 60% in 2017.
At the same time, confidence among businesses that they can deal with cybersecurity in practice is declining. It’s easy to understand why; new trends and technologies equal a steady stream of new threats, forcing enterprises to constantly adjust their capabilities to keep up.
Confidence in cyber resilience measures slipped from 2017 to 2019


By far the biggest change over the past few years is in the nature of systems businesses are trying to secure. Ubiquitous connectivity has made systems easier to control and opened more possible entry points for bad actors. The rise in working from home and online activity driven by the pandemic has highlighted connectivity’s downsides as well its advantages. A recent poll of US technology executives, for instance, found 89% of organizations had been targeted by COVID-19 related malware.
What’s more, the pandemic has changed behavior in a way that has negative security implications. “For many people, the only way to socialize now is digitally,” says Harinee Muralinath, Capability Lead at Thoughtworks. “People are online more often, they’re socializing more on digital platforms and they’re frightened about the current situation, so there’s definitely a higher hit ratio on clickbait. There’s been a rise in intelligent phishing targeting the human fear around the pandemic.”
With the rate of threats unlikely to slow down, the only effective response is to make security equally dynamic. Security needs to scale as the boundaries of the enterprise, and the threat landscape, change - a capability that traditional security frameworks and off-the-shelf solutions lack.
“As long as security is just a box to check, it’s not going to drive the necessary outcomes,” says Jim Gumbley, Cyber Security Principal at Thoughtworks. “It requires a shift in culture.” But where should organizations start?

“As long as security is just a box to check, it’s not going to drive the necessary outcomes. It requires a shift in culture.”
Jim Gumbley
Cyber Security Principal, Thoughtworks
Know your weak spots
Step one is recognizing how the nature of threats has shifted, and facing up to the new security realities being created by the proliferation of connectivity, data and cloud-based computing models.
Cloud computing
The mass migration from in-house servers to cloud-based architecture comes with some inherent security advantages. Given it’s foundational to their business model, major cloud service providers invest in and prioritize security in a way few enterprises can match, so any cloud-hosted systems have a strong base level of defense.
“There’s definitely a plus in going to the cloud in that you do benefit from the nearly always superior capabilities of major cloud providers to protect their hardware and networks,” says Robin Doherty, Lead Security Architect, Thoughtworks.
The problem is, some enterprises assume entrusting their assets to a cloud provider means security is effectively covered. A recent study of firms in four major Asia Pacific markets found over half believed all security infrastructure requirements are handled by their cloud service provider, and just 40% understood security was a shared responsibility. This is despite the fact that, as Doherty points out, most cloud providers are explicit about where their duties end - and “give their customers a lot of scope” to introduce vulnerabilities.
Common Misconception of Responsibility
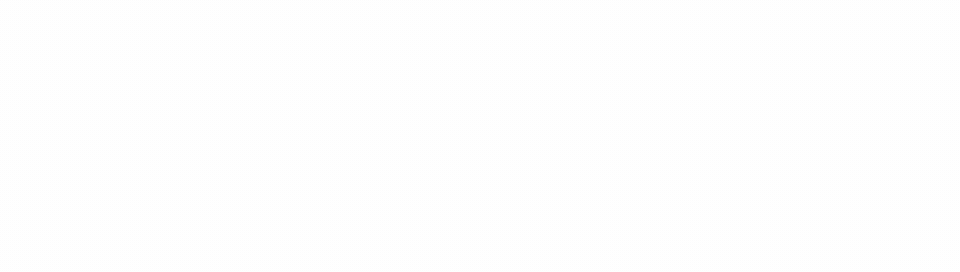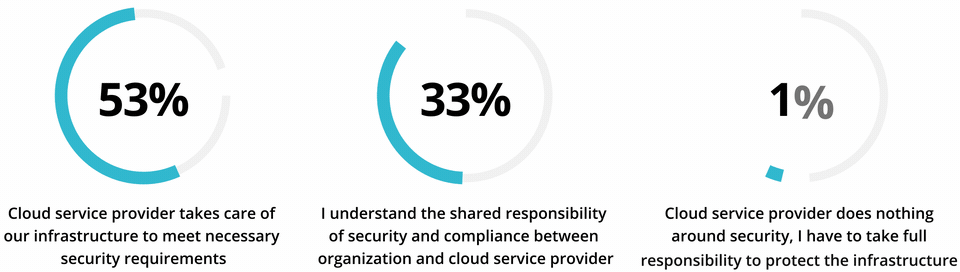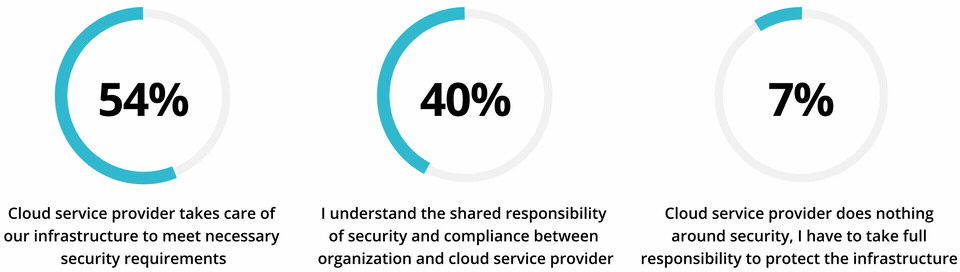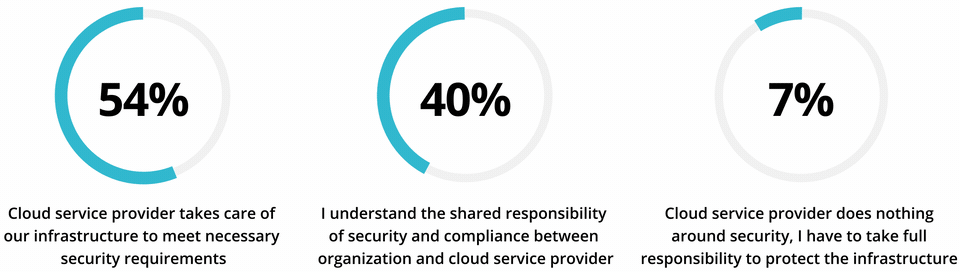

There’s also a basic technical point about cloud that makes it riskier in some respects. “If you’ve got an on-premise network and fail to configure it correctly, not just anyone can get access and there’s only so far a problem can go, because there’s a degree of physical separation,” Gumbley explains. “Cloud is designed to connect to the internet, so even small errors can have a huge blast radius.”
Cloud means any system is effectively only as strong as its weakest link. And as Neelu Tripathy, Security Practice Lead at Thoughtworks notes, sometimes those links are very weak indeed.
“Because everything is so distributed, if you look at it from the attacker perspective, it’s become a lot more difficult to go after back-end systems,” she says. “Attacks are moving outside, to individuals. Social engineering, phishing and the like are proving a lot of help for attackers to get that first foot forward into the organization.”
Cloud-enabled connectivity is also a double-edged sword in that it makes many of the capabilities and resources that can help companies available to bad actors.
“With the rise of open source, cloud systems with high processing power, and languages that make scripting easy, you don’t need to be a great programmer to write a bot that will sniff around to test how vulnerable a system is,” says Muralinath. “And if you’re using underlying platforms or containers you pulled off the internet, there are many people who have already done the same, which means those tools come with known vulnerabilities. A bigger repository of knowledge has been opened up for attackers to use as well.”

“Because everything is so distributed, attacks are moving outside, to individuals. Social engineering, phishing and the like are proving a lot of help for attackers to get that first foot forward into the organization.”
Neelu Tripathy
Security Practice Lead, Thoughtworks
Data
Along with the ascent of cloud platforms, there’s been a sea change in the way consumers view their data that’s forced companies to reckon with data security.
“Companies are attaching more and more importance to privacy, not necessarily because they care a lot more about their customers than they did 10 years ago, but because the attitudes of society, governments and jurisdictions have changed,” Doherty says.
Fewer organizations are engaging in potentially hazardous habits like using customer information in test environments, or sharing sensitive data on USB sticks, Doherty notes. As a result, in many companies, data protection is growing stronger. But that doesn’t change the fact that the exponential growth in the volume of data, and the use of data for business intelligence, means it’s a much larger and more tempting target.
Applying data-based tools like AI and machine learning to drive business decisions can also introduce new dimensions of risk, according to Gumbley.
“Having AI systems that can explain why they’ve made a particular decision is very difficult,” he says. “If someone is able to game that system you may not even be able to detect it because you didn’t understand why it made a decision in the first place. In order to secure any system, you need to understand it, and that can be a challenge given the way certain decision support systems are deployed.”

“In order to secure any system, you need to understand it, and that can be a challenge given the way certain decision support systems are deployed.”
Jim Gumbley
Cyber Security Principal, Thoughtworks
The IoT
Greater adoption of the Internet of Things (IoT) has enabled companies to automate many critical functions, including in some cases security itself. But as more connected devices are deployed at critical points in the production process, or come into closer contact with employees and customers, the enterprise’s attack surface expands.
“I’ve even heard about devices like thermometers being hacked,” says Muralinath. “That alone can be enough to bring someone inside a network where they can access other devices and data. The fact that we’re so connected is something that’s also increased the threat landscape.”
Particularly when it’s part of the systems that govern critical assets like health facilities or infrastructure, IoT security “becomes critical, because the impact is direct and it’s physical,” says Tripathy.
Unfortunately, “a lot of IoT products have poor security,” Doherty says, shipping with problematic default configurations or passwords that may never be optimized or updated.
This is particularly worrying when more people are working remotely and as the lines between personal and work devices have blurred. A new study by the US National Cyber Security Alliance, for example, showed about a third of connected device users don’t always bother to change default passwords and that half regularly access unsecured WiFi networks.
Respondents that change connected device password settings from the default manufacturer settings
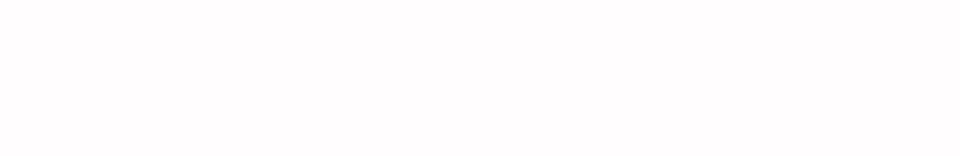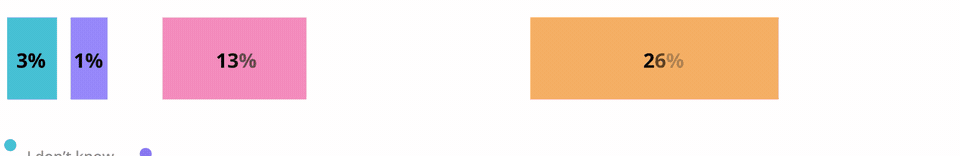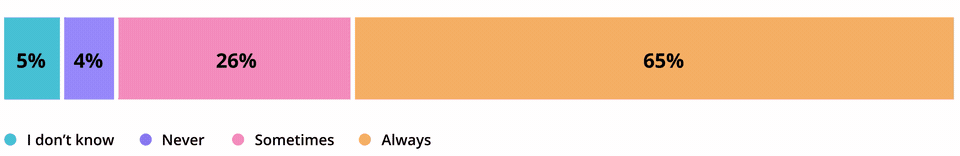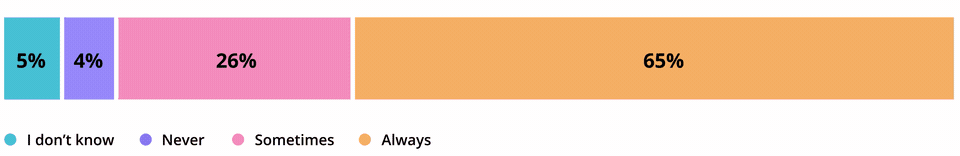

That argues for enterprises to work toward creating a ‘zero-trust’ architecture, meaning “you don’t trust devices just because they’re on your network, and you don’t trust everything that a system does just because you created that system,” Doherty explains.
Complex supply chains
Another common vulnerability is the tendency of companies to concentrate on their own practices while neglecting or underestimating the risks posed by increasingly tangled vendor, production and supply chain networks.
In many cases, employees may not be aware of all the different organizations that stand behind the systems they use. Across the vast spectrum of software service providers, suppliers and distribution partners, Gumbley says, “there only needs to be one weak link in the chain, one that hasn’t got good software security standards,” for a problem to surface.
Unfortunately there are no real shortcuts to addressing this; it requires deep scrutiny of service agreements and the standards held by partners for possible shortfalls.
“Making sure you’ve got good standards compliance across your supply chain can be like watching paint dry, but it can make a big impact,” Gumbley says.
From security policies to security culture
Technology, zero-trust architectures and training can all help enterprises manage emerging security challenges, but according to Thoughtworks’ experts, even the most capable teams can only hope to construct a partial safety net, and occasional failures are all but inevitable.
Instead of focusing on the unrealistic target of making the organization impregnable, business leaders should prioritize changing the way security is perceived. “The biggest problem with security is mindset,” says Muralinath.
The first perception to tackle is that security is the exclusive responsibility of a stand-alone team. “You can no longer have a central security team that acts as a gatekeeper, deciding what can go to production, following a checklist, reviewing whatever’s deployed every six months, and telling delivery teams what to do,” says Doherty. “People are deploying all the time now, and the old style of controls don’t work anymore.”

“You can no longer have a central security team that acts as a gatekeeper, reviewing whatever’s deployed every six months. People are deploying all the time now, and the old style of controls don’t work anymore.”
Robin Doherty
Lead Security Architect, Thoughtworks
“Siloed, compliance-led security with lots of focus on hardware and firewalls - security in the corner, you could call it - is almost a bit of theatre or a fig leaf to show people that something is being done,” agrees Gumbley. “It leaves enterprises vulnerable to getting washed away by all the risk out there.”
The more future-proof approach is to position security as a collective effort, in which every function, having something to lose, also has a role and a say. “Security has to be based on different perspectives,” Gumbley explains. “The technologists might not understand the particular value of a certain set of data, but another team will because they live and breathe it. Legal, HR or other parts of the business often have a better idea of what’s at stake and what can actually go wrong than someone who knows how to configure a firewall.”
“Enterprises can foster a more collaborative security culture by deploying members of the security team to act as internal consultants,” Doherty says. Having security work within project teams embeds defense mechanisms throughout the development process and avoids the “security sandwich,” where checks are applied only at the beginning and end of a project with potentially painful results.
Security sandwich


“Adding a security person into a cross-functional team means you’re doing a better job of reducing risk as you go,” he explains. “You don’t end up in a situation where the project or requirements change over time, and when the security team comes back towards the end, they identify a bunch of problems. And then you have to have a horrible conversation about whether you need to postpone going live.”
Making security more democratic may involve delicate organizational changes that reshape the balance of control and accountability, Muralinath says. That argues for the process to be accompanied by senior management support and a certain amount of outreach to all levels of the enterprise.
“People closer to the ground, like product owners, may not understand the responsibility for security is now in their hands as well,” says Muralinath. “There are many times that they might keep putting things off, saying ‘let’s just build a feature first, let’s get this out the door and we’ll worry about security later.’ There’s a lot of education that needs to happen at that middle level of management.”
“It’s important to educate and create a good amount of awareness around security techniques,” Tripathy agrees. “Telling employees exactly what is critical for the organization, what the business assets are, what data can and can’t be disclosed publicly. When the new normal is virtual and social, we need to develop critical thinking in employees in general - not only when they’re coding, but when they’re engaged in day to day activities.”
Confronting the talent deficit
A major advantage of building security capabilities collectively is that it can help the enterprise cope with the real, and pressing, shortage of cybersecurity talent.
According to global IT governance association ISACA over 60% of organizations believe their cybersecurity teams are understaffed, and 66% find it difficult to retain cybersecurity staff, mainly because they are regularly recruited away.
State of Cybersecurity 2020


While cybersecurity experts will always have their place, “there’s a problem when you think of security in isolation,” notes Muralinath. “You need to build the talent in existing teams so they understand the extra things they need to do to put security in place. It’s not the number of security specialists you should be increasing, but the number of developers or others who also take care of security as part of a group, so you increase the security space organically.”

“There’s a problem when you think of security in isolation. You need to build the talent in existing teams so they understand the extra things they need to do to put security in place.”
Harinee Muralinath
Capability Lead, Thoughtworks
“It’s certainly been our experience at Thoughtworks that there’s a fair number of people who may not have security roles, but care deeply about security and want to grow their security capabilities,” agrees Doherty. “If you can identify who those people are and give them a role to play in that transformation, it’s hugely beneficial.”
“If you can’t hire all the good people you need, grow them,” says Gumbley. “Much like DevOps in the past, there’s a massive community around security now, with all kinds of resources and opportunities to collaborate and learn. It’s more diverse, exciting and innovative than it has been at any point in my lifetime. Security’s not boring anymore.”

“There’s a massive community around security now, with opportunities to collaborate and learn. It’s more diverse, exciting and innovative. Security’s not boring anymore.”
Jim Gumbley
Cyber Security Principal, Thoughtworks
New measures of performance
According to Doherty, edicts or controls pushed from the top down won’t cultivate the shared sense of security companies should be aiming for. “It requires building behaviors and norms, and for that to work, it’s not particularly helpful for the C-level to say ‘these are the rules,’ he says. “They have to make space, and they have to adjust incentives.”
Specifically, incentives need to change in a way that shows the ultimate aim of security is no different than other functions in the organization - to deliver value. “Often I hear product owners talking about needing to deliver user value, not security work,” Doherty explains. “But security protects user value, and the reduction of risk is an increase in expected value.”
At many organizations, measures of security performance reflect the perception that it’s a control mechanism or stopgap, rather than a value contributor. “Security KPIs tend to be very badly designed,” Doherty says. “If you’re asking people to reduce the number of incidents, there’s an easy way for them to do that - they just don’t tell you about what’s happening. That means you never get better over time.”

“Often I hear product owners talking about needing to deliver user value, not security work. But security protects user value, and the reduction of risk is an increase in expected value.”
Robin Doherty
Lead Security Architect, Thoughtworks
Similarly, if security teams are incentivized only to reduce risks, they’ll often be left at odds with the rest of the organization, especially delivery teams, who are usually motivated to get things released as quickly as soon as possible.
The answer, according to Gumbley, goes back to making risk something everyone is measured against. “Established best practice around risk management is the solution to the problem,” he says. “That could be a risk register - a prioritized set of risks that you’re aligned around as a business. The important thing is that a set of risks is owned by the business, not by the security team.”
Muralinath meanwhile believes more metrics should be constructed around where and when vulnerabilities are detected. “How late did you find the defect - during early development, or production? Your pipeline should be set up such that your build doesn’t proceed to a certain environment if certain kinds of tests fail,” she says. “What you’re really measuring is the effectiveness of those programs, as well as the knowledge and awareness of your teams.”
When the inevitable happens
Regardless of how security is evaluated and encouraged, it’s all but certain that every business will eventually have to confront an incident or breach. Yet there’s no need for that to equate to disaster if the enterprise has taken care of what Gumbley calls “step zero - planning, practice and preparation.”
“If you haven’t prepared you’ve got no chance,” he says. “It’s worthwhile to assume you’re going to get breached and think about who you’re going to call in that kind of situation, whether for legal support, data protection, or a technical response.”
In case of an incident, the immediate priority should be identifying and addressing the vulnerability, says Tripathy. “If it was an older version of software that was exploited, update that; or if it was a database exposed in the backend, close the network boundary.” But right after that comes “going out and informing your customers - and being transparent about it.”

“If your customer information has been affected, it’s best to disclose that accurately, and give concrete solutions, so you’re not just making customers aware, but building trust at the same time.”
Harinee Muralinath
Capability Lead, Thoughtworks
“If your customer information has been affected, it’s best to just come out in the open and disclose that,” agrees Muralinath. “It’s important that you understand the depth (of the breach) enough to be able to disclose it accurately, and give concrete steps on what’s next. You need to present solutions along with information on the problem, so you’re not just making customers aware, but building trust at the same time.”
Once the dust has settled, a post-mortem can turn an incident into an opportunity to learn, but shouldn’t descend into a blame game. As Tripathy points out, most incidents “are not just because of one layer being breached; it’s generally a misconfiguration of multiple layers.” That makes it difficult to point the finger at a single person or point of failure.
“You’ve got to do some kind of retrospective, even for near misses,” agrees Gumbley. “But at the end of the day, assigning blame is not going to help you prevent the next incident. Breaches are so complex that there’s always multiple causes, and with many systems now a multi-vendor patchwork of different organizations and labor frameworks, it can be a real minefield.”
The lean security cycle
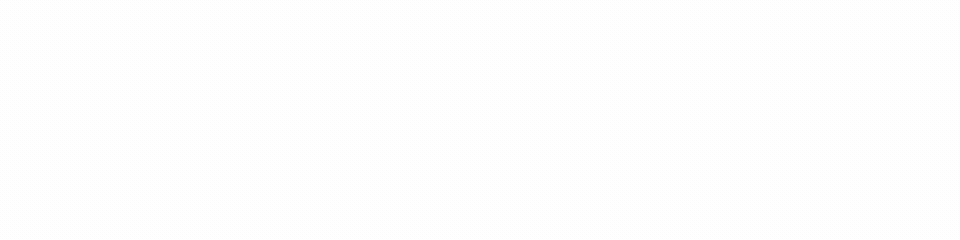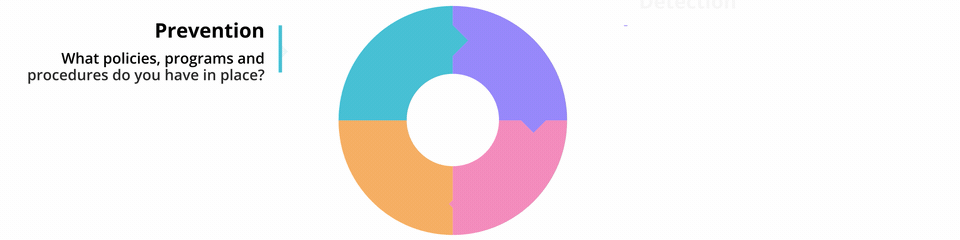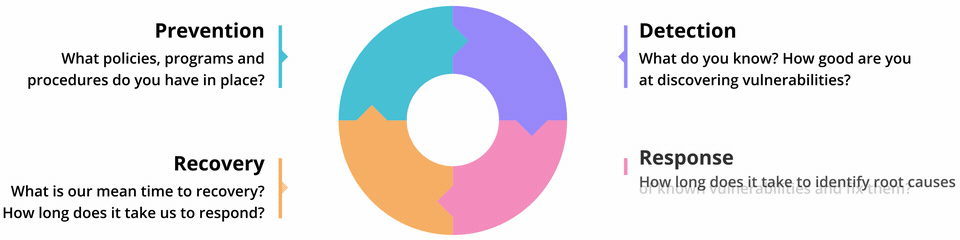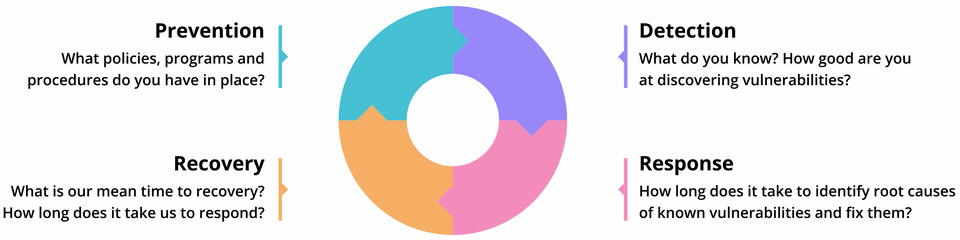

“The big priority should be to learn from small incidents,” says Doherty. “There’s a temptation when you’re chasing progress to just move on, but it's important to resist that. Acknowledge that you made a mistake and luckily you didn’t end up on the front page of the news this time, but with a few variations you could have. When responsibility for security is distributed, everyone needs to be aware of these developments. You should be sharing not just information, but the story about how it happened, making it relatable so people can see how they could get themselves into the same situation.”
Conclusion: Planning for the unknown
This year has been a good reminder that no enterprise can predict what risks or security threats may lurk around the corner - but according to Gumbley, as companies plan for 2021, that’s no reason not to try.
“You should be constantly scanning, brainstorming and trying to spot potential threats, measuring how much impact or risk they might involve, and if they’re significant enough, acting,” he says. “(Ransomware attack) WannaCry was a perfect example - there was a six-month grace period where organizations could have seen it coming and patched some of their servers. Will you always see what’s coming perfectly? No chance. But can you do better than passively waiting? Absolutely.”

“Will you always see what’s coming perfectly? No chance. But can you do better than passively waiting? Absolutely.”
Jim Gumbley
Cyber Security Principal, Thoughtworks
Automation, particularly in the form of infrastructure as code, and in areas like testing, threat detection and alerting, has significant potential to help enterprises enhance security by accelerating processes and reducing instances of human error.
But Thoughtworks experts caution against rushing to invest in the latest AI-enabled security solutions. “It’s very easy to get caught up in thinking you need AI to solve a problem because it sounds like it’s going to be a silver bullet,” Doherty says. “But it isn’t, and in most cases there’s a lot more that companies can be doing to understand what’s going on in their systems before they start worrying about it.”
“Where you have parameters defined in a system that you can identify and measure, AI can be leveraged, but it depends on what’s at stake,” says Tripathy. “There are always things that are better done manually. A basic principle in security is that the cost of controls you’re putting in can’t be higher than the value of the business asset you’re trying to protect.”

“A basic principle in security is that the cost of controls you’re putting in can’t be higher than the value of the business asset you’re trying to protect.”
Neelu Tripathy
Security Practice Lead, Thoughtworks
While risks continue to rise, experts also see plenty of room for hope about the future of enterprise security, as more organizations experiment with proactive, even inventive, steps.
“I definitely see people investing more in security, and if nothing else, top management is really concerned, which means if you’re consulting on security, they’ll listen,” says Muralinath.
Tripathy points to ‘bug bounty’ programs, in which companies reward third parties for discovering issues or vulnerabilities, as a promising example of how security practices are starting to push the envelope.
“Organizations are beginning to understand that they may not have the resources to perceive all the attacks that are introduced or problems latent in their applications,” she says. “There are a lot of assumptions in your thinking when you’re an insider, so external views can show you something very different. It definitely needs to be done carefully, but it’s a very smart way of looking at security, and makes me optimistic about what’s to come.”
Trends like these underline the theory that when it comes to shoring up defenses against emerging threats, enterprises may benefit most from efforts to broaden perspectives.
“Controls are all well and good, but there are still a lot of people who don’t think about security in their decision-making processes,” Doherty explains. “It’s important to build the ability to assess risk generally, not just security risk. It’s a difficult thing because the scope of what you need to worry about as a human or a technologist has grown; there are more and more things that each of us needs to internalize and take a little bit of responsibility for. But the power of that understanding can’t be overstated.”

“It’s important to build the ability to assess risk generally, not just security risk. It’s a difficult thing because the scope of what you need to worry about as a human or a technologist has grown. But the power of that understanding can’t be overstated.”
Robin Doherty
Lead Security Architect, Thoughtworks
By JoJo Swords
Perspectives delivered to your inbox
Timely business and industry insights for digital leaders.
The Perspectives subscription brings you our experts’ best podcasts, articles, videos and events to expand upon our popular Perspectives publication.