Perspectives
Sometimes, lightning does strike twice. In May this year, an employee working for a multinational in Hong Kong transferred over US$500,000 to various bank accounts based on instructions in an earlier meeting from who she thought was the firm’s CFO – but who turned out to be a digital recreation created and manipulated by sophisticated fraudsters. Just months earlier, a nearly identical ‘deepfake’ scam cost UK-based design and engineering giant Arup’s office in the city over US$25 million.
Incidents like these demonstrate the speed and extent to which the security threats faced by enterprises are changing. Cyberattacks continue to rise; research by CrowdStrike charted a 75% year-on-year jump in cloud environment intrusions in 2023 alone, and a similar spike in victims named on cybercrime-linked sites that leak personal details.
An evolving international threat landscape
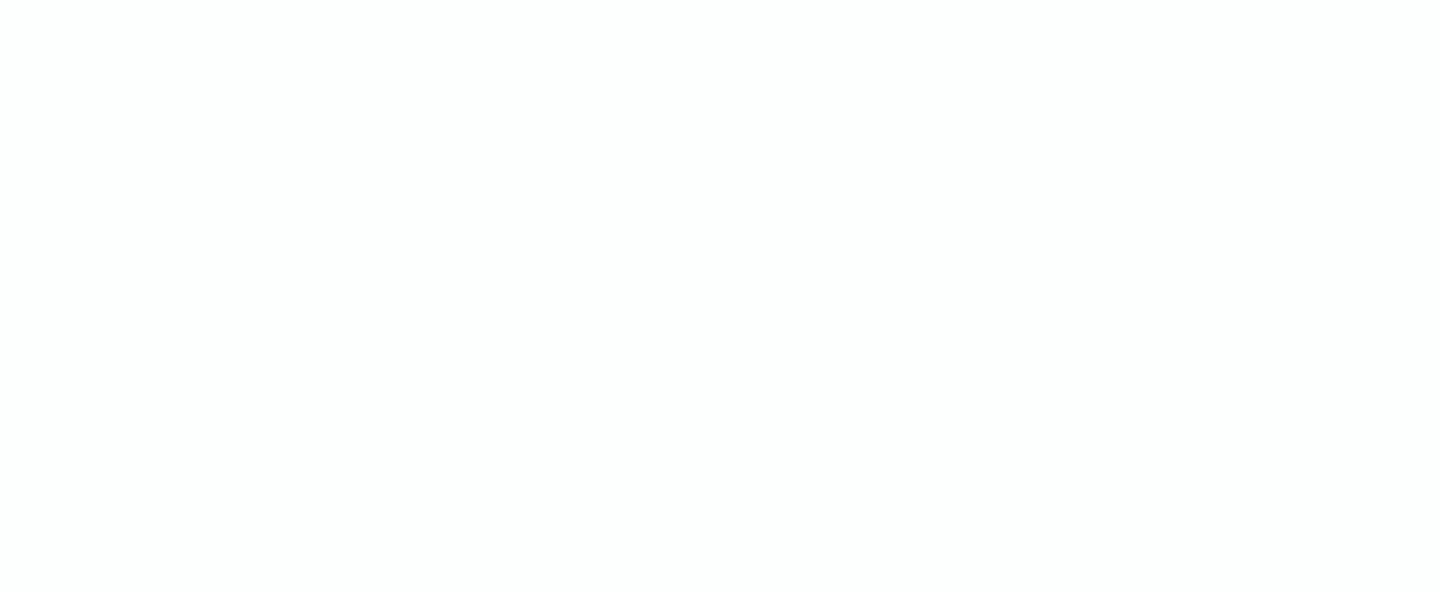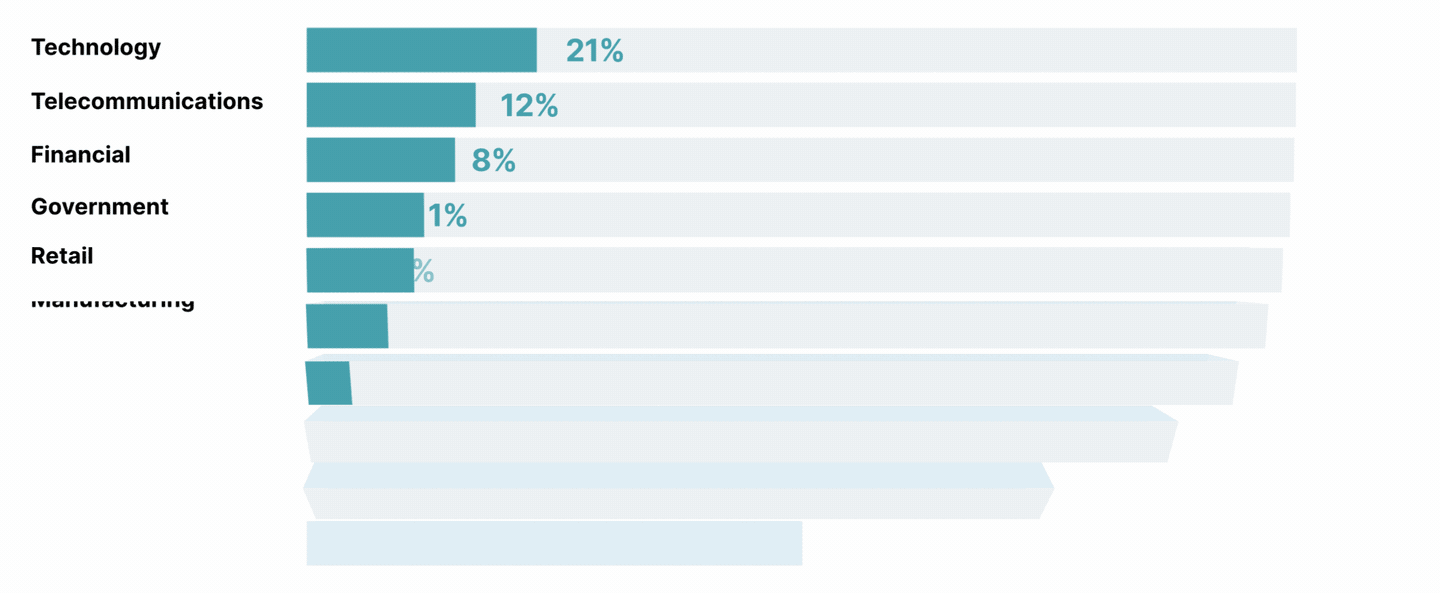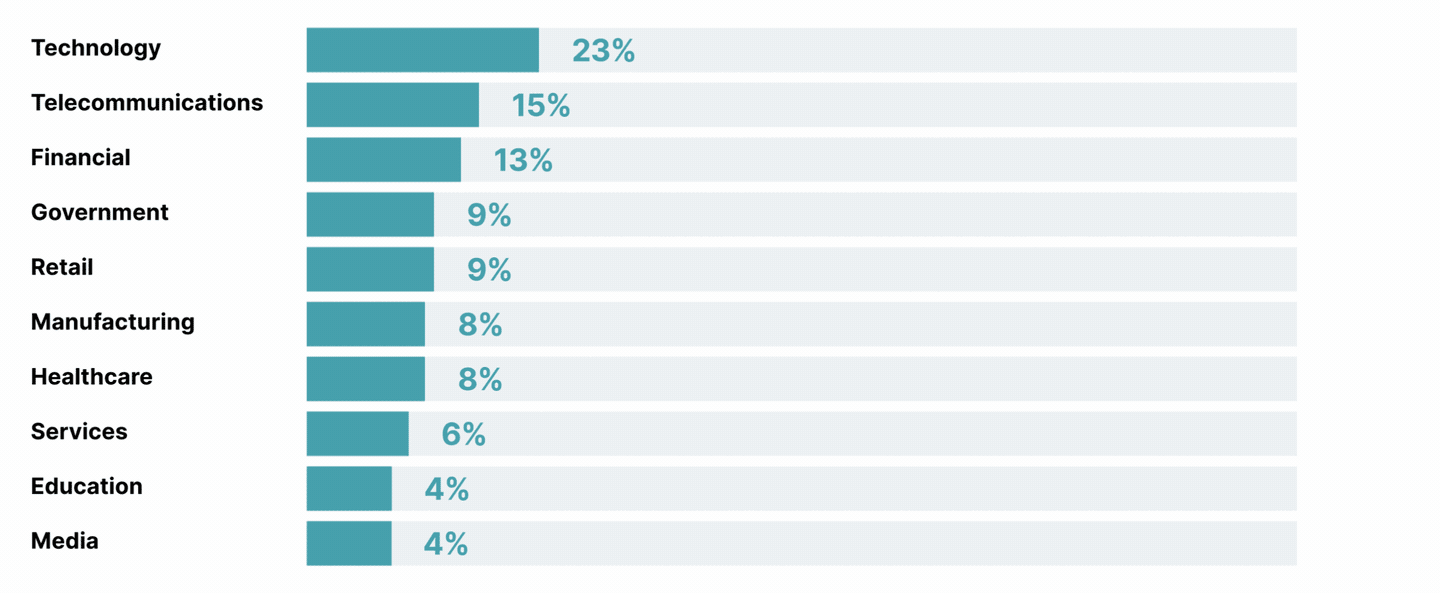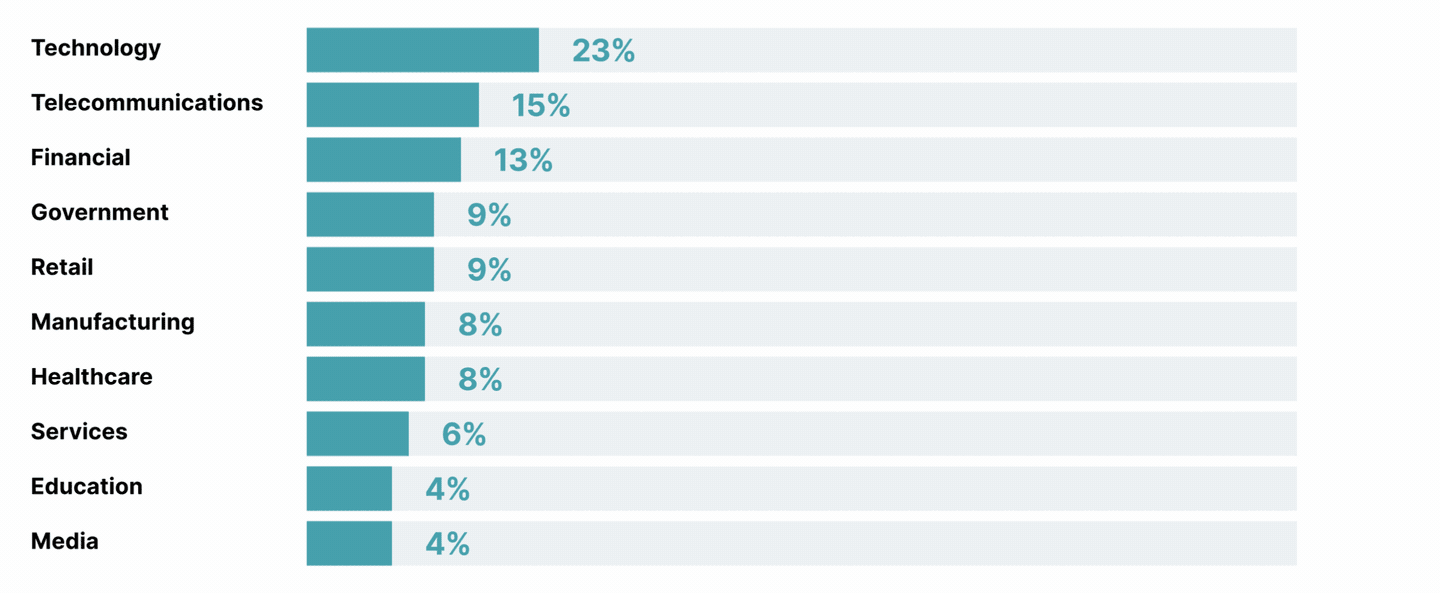
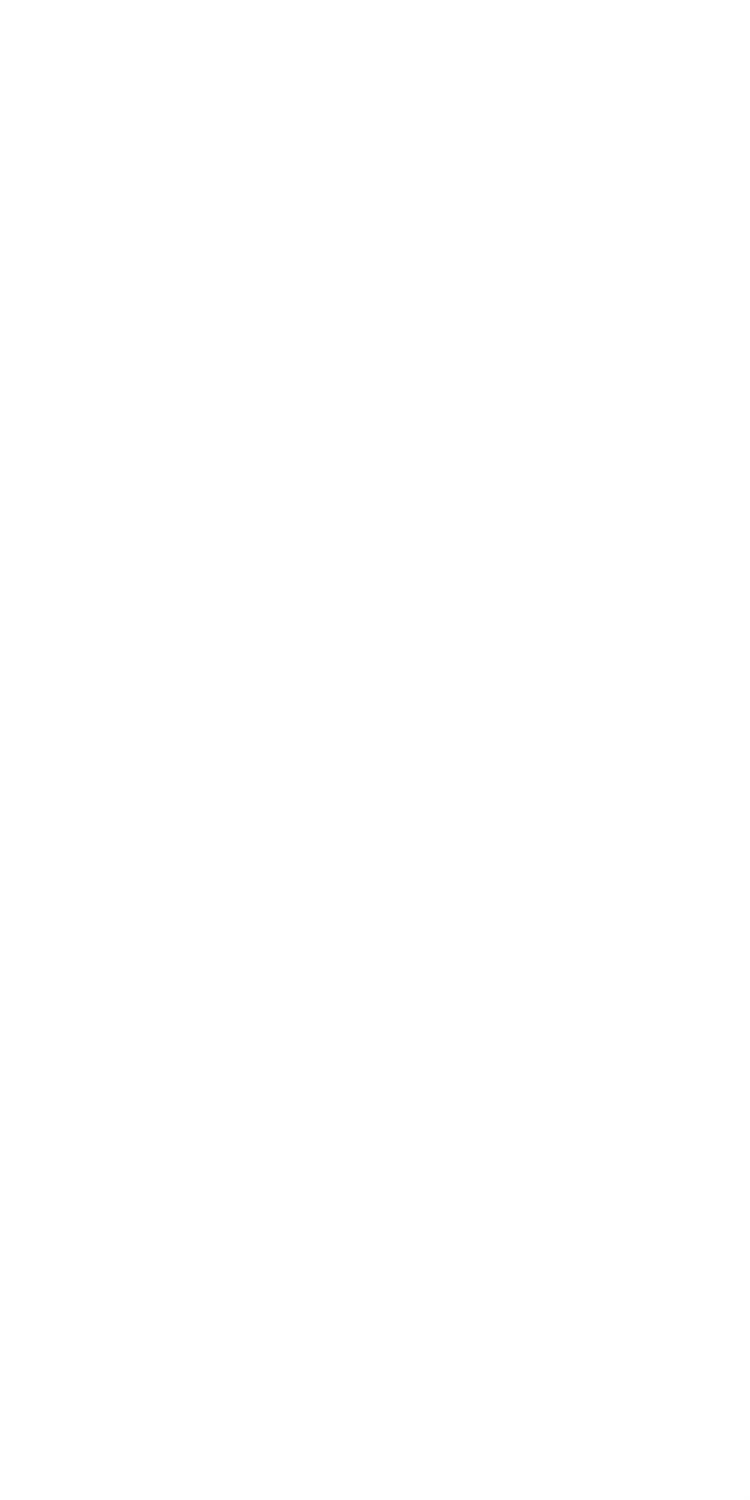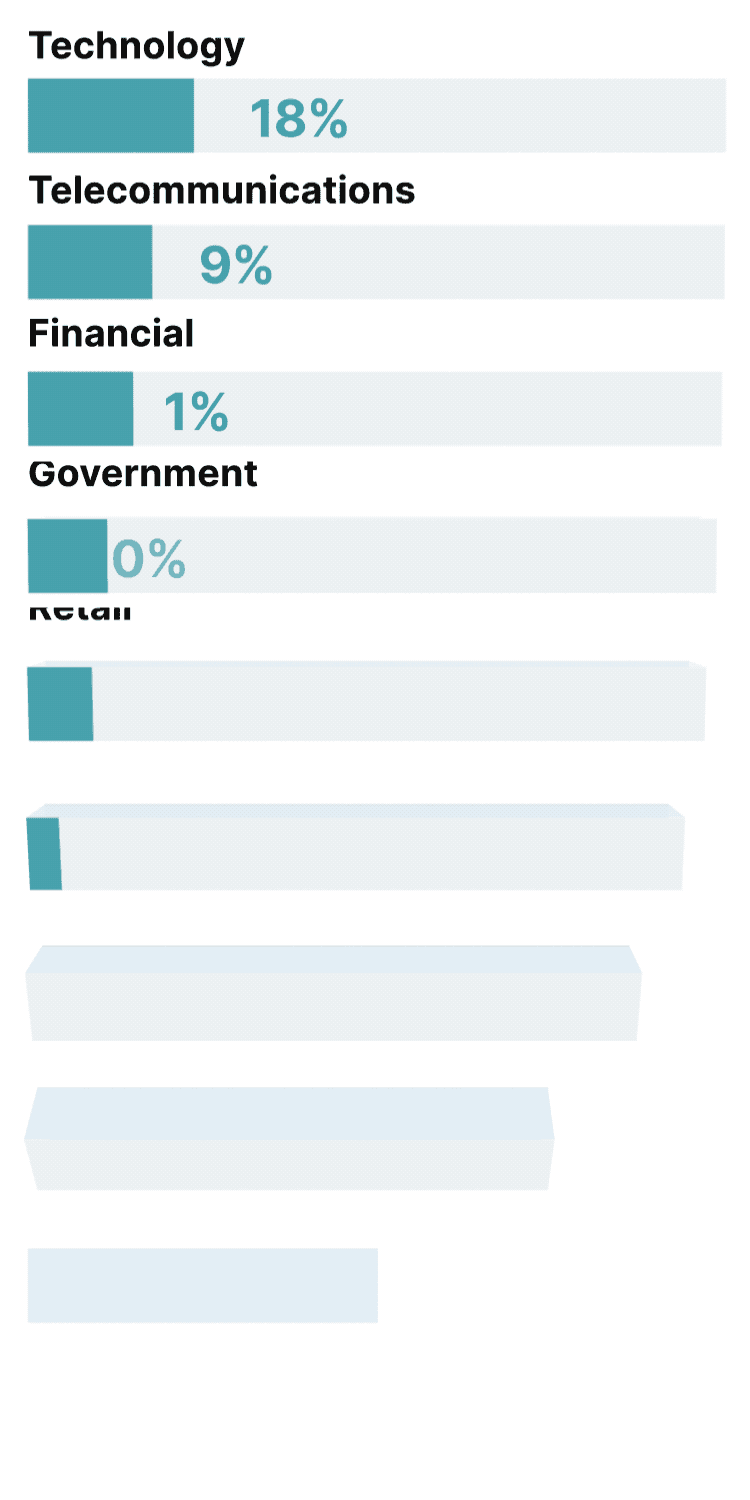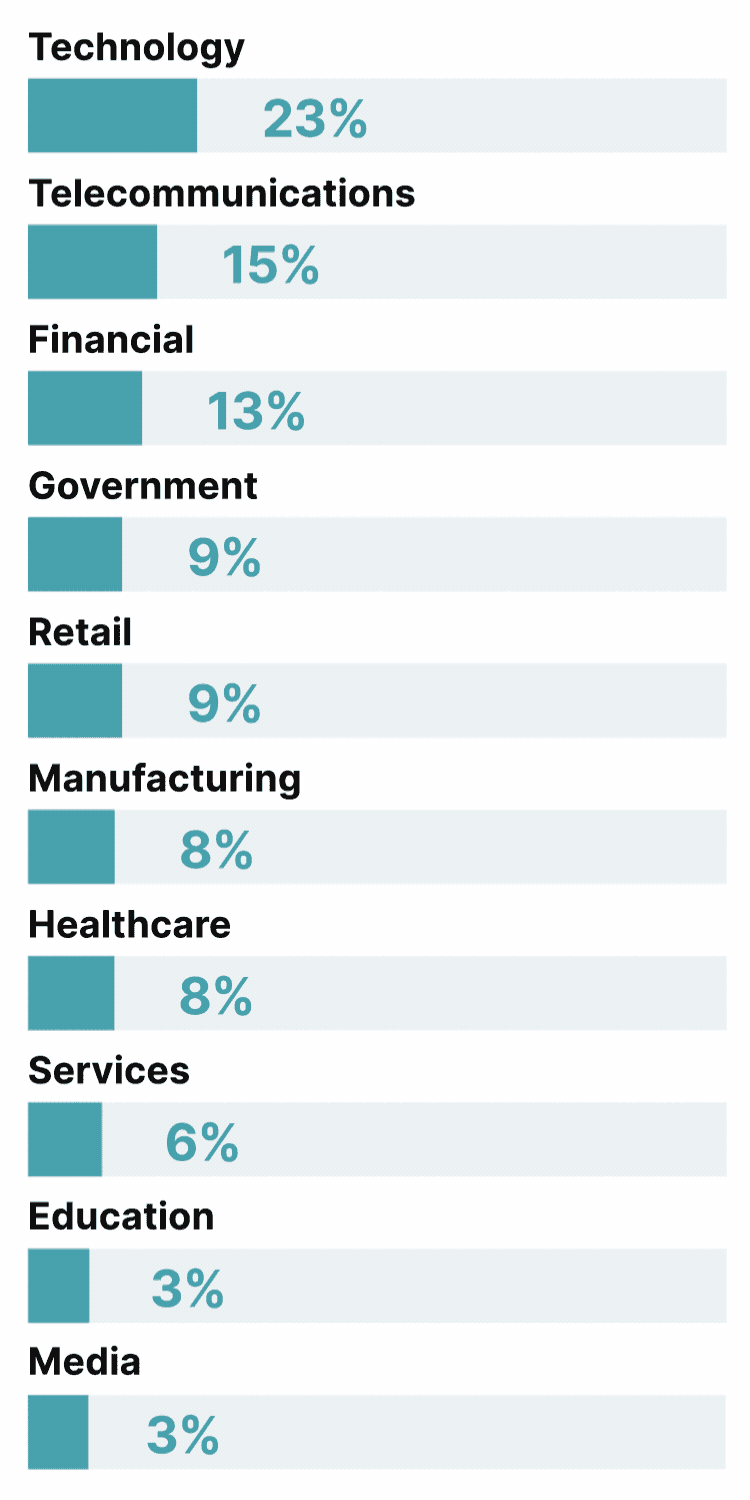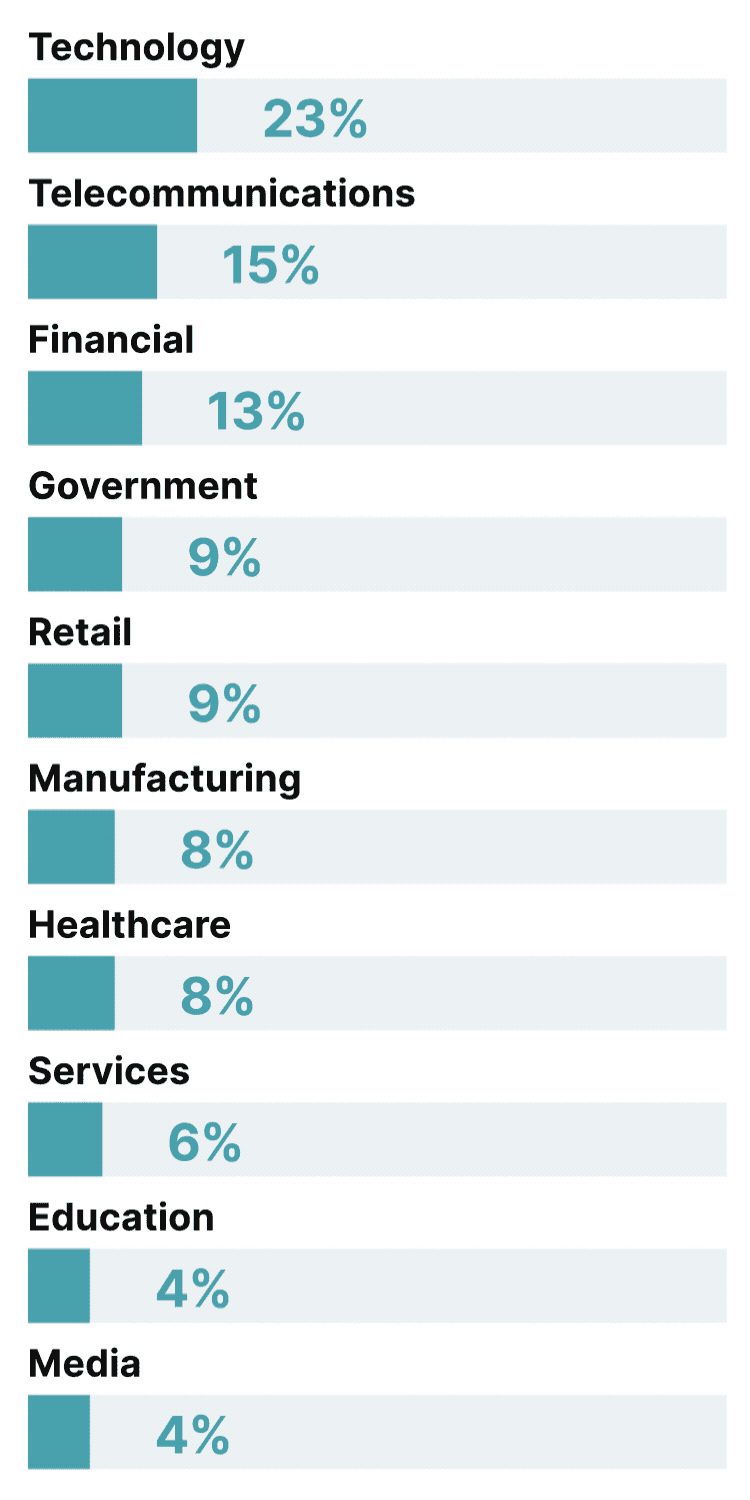
Yet according to Thoughtworks security experts, more alarming than the quantitative growth in threats is the way threats are becoming more diverse, sophisticated, and potentially devastating.
“One of the major changes in the cybersecurity landscape is that cybercrime has become more organized,” says Robin Doherty, Principal Consultant, Global Head of BISOs & Business Information Security Officer (BISO), APAC, Thoughtworks. “There are now a lot of professional cybercrime organizations who even have the equivalent of an HR department, and are operating in countries where they can get away with it. Because of their scale, these organizations can invest in their operations – for example providing ransomware as a service, where they offer for a subscription the use of their malware and their expertise as negotiators, all while protecting their clients’ identities.”

“There are now a lot of professional cybercrime organizations who even have the equivalent of an HR department, and are operating in countries where they can get away with it. Because of their scale, these organizations can invest in their operations."
Robin Doherty
Principal Consultant, Global Head of BISOs & Business Information Security Officer (BISO), APAC, Thoughtworks
“Externally, organizations are at risk on multiple fronts, from advanced persistent threats (APTs) and state-sponsored attacks that focus on obtaining sensitive data and destroying key infrastructure, to cyberattacks that capitalize on vulnerabilities in the supply chain,” says Lu Yang, Thoughtworks’ Head of Incubator Service Line Security, China. “Ransomware and extortion are also becoming major concerns. Companies that refuse to play along might be threatened with further attacks that target key infrastructure, posing a threat to their ability to provide basic services.”
Many new challenges are emerging as enterprises become more external-facing, outsourcing more aspects of their infrastructure or linking systems and applications with more third-party providers. The proliferation of connected devices and migration of work to non-office locations is another complicating factor.
“Building boundaries for information systems has to incorporate the element of risk that is introduced with the work from home model or in a shared office environment,” notes Lilly Ryan, Global Secure Delivery Strategy Lead, Thoughtworks. “We need to be thinking about perimeters in a flexible way. We can no longer rely on physical office boundaries, unless we're in very specific, highly regulated environments.”

“AI is what our clients are asking us about the most, and it boils down to two main questions. The first is: What threats does AI bring up that didn't exist five years ago? And the other is: How can I use AI to help my business do security better?”
Lilly Ryan
Global Secure Delivery Strategy Lead, Thoughtworks
What’s more, in the same way it’s rewriting other functions, artificial intelligence (AI) is poised to transform the security landscape – for better, and for worse. “AI is what our clients are asking us about the most, and it boils down to two main questions,” says Ryan. “The first is: What threats does AI bring up that didn't exist five years ago? And the other is: How can I use AI to help my business do security better?”
In light of these changes, there’s a danger that legacy approaches to security will not be able to keep up. These trends will require businesses to retool their policies, technologies and practices to ensure they build and maintain trust with customers and other stakeholders – not just to protect the enterprise, but also to foster the confidence that creates competitive advantage. After all, when companies are seen to be dropping the ball on cybersecurity, customers are prepared to vote with their feet.
i. AI changing the security picture – and possibilities
On a more positive note, the growing prominence of cybercrime and high-profile security incidents mean there’s more security awareness among business leaders than ever. “We’re seeing more and more understanding of security as a business concern, not just an IT concern,” says Doherty. “Security gets talked about a lot at the highest levels of an organization these days.”
For many senior executives, the security implications of AI, and especially GenAI, have become front of mind. In one survey of business and tech leaders by PwC, almost 70% had plans to use GenAI for functions like incident risk and reporting over the next 12 months – but over half also expected GenAI to fuel “catastrophic” cyberattacks over the same period.
Yang notes AI allows cybercriminals to automate tasks like finding vulnerabilities, launching brute-force attacks, and crafting convincing phishing scams, making such attacks faster and vastly more scalable. “AI-driven malicious software will also be more difficult to detect, as it continuously adapts to evade traditional security measures,” he explains.
As the recent cases in Hong Kong demonstrated, AI-generated content also presents a massive challenge to the standard wisdom around identity and identity verification.
“It will become increasingly difficult to get real information, or to make judgments as to information’s trustworthiness,” says Yang.

“It will become increasingly difficult to get real information, or to make judgments as to information’s trustworthiness.”
Lu Yang
Head of Incubator Service Line Security, Thoughtworks
As Ryan puts it: “The questions GenAI really brings up are: What mechanisms do we have to trust that someone is who they say they are? And what does that mean for the decisions that we make based on that information? We have to be extra careful in thinking about what information we trust, what can be faked and what can't, knowing that it's not only technically possible for fakes to happen in an academic sense, but also possible for fairly average criminals to create them, with conventional off-the-shelf technologies.”
“The main fear that exists at the moment is that with the advent of large language models (LLMs), it will be easier to quickly come up with unique attacks that may be more likely to succeed, because models can integrate information about how specific recipients or companies respond to information or how they communicate,” says Doherty. “For example, if you took all of Thoughtworks’ internal data or internal emails and fed them into an LLM, you could generate very convincing emails in the style of Thoughtworks and send them to employees.”
This means some of the standard advice to employees on how to spot scam or phishing attempts will need to be updated. “We need to revisit assumptions about things like what a phishing email looks like,” Ryan points out. “If we’re telling people they’re usually full of typos, well – ChatGPT doesn’t really make typos.”
Thinking further out, companies will also have to consider the security implications of integrating AI into features like chatbots. Not only can these veer dangerously ‘off script’ – Canadian flag carrier Air Canada was recently held liable for a chatbot giving a customer erroneous advice – but as Ryan notes, to build or run chatbots many companies will upload massive amounts of data and documentation to third-party services, increasing vendor and supply chain security risks.
Yet while being conscious of the risks, it’s also important for organizations to remember AI can play a positive role. “AI is excellent when it comes to determining patterns and bridging the gaps between human and machine communications, so it can make incidents easier to query or analyze,” says Ryan.
“AI can be a great cybersecurity ally,” agrees Yang. “Its ability to analyze vast amounts of data and recognize patterns makes it the ideal tool for calling out suspicious activity, and enhancing the speed and accuracy of threat detection.”
Doherty counsels business leaders to keep both AI’s security risks and potential in perspective. “It’s still early days,” he says. “Many security tools will talk up the benefits of their approach but are based on basic logic. Snake oil is very prevalent in the security industry, and you find a lot of vendors just attaching the latest buzzwords to their products.”

"Snake oil is very prevalent in the security industry, and you find a lot of vendors just attaching the latest buzzwords to their products.”
Robin Doherty
Principal Consultant, Global Head of BISOs & Business Information Security Officer (BISO), APAC, Thoughtworks
ii. Constructing an effective security posture: Technology, models and practices
So what constitutes a ‘good’ security approach or investment? According to Thoughtworks experts, business leaders should adopt a holistic approach that spans people, process and technology.
“Don't focus on technology at the expense of everything else, which is a common mistake,” says Doherty. “Organizations that are less mature from a security point of view tend to go to technology first. There are some basic security tools that you need, but you also need to invest in your people and your processes.”
“Generally, organizations overestimate the reach and effectiveness of security products and automation, leading to many hidden threats,” agrees Yang. “It’s only by considering the multiple factors that come into play and adopting a proactive and adaptive approach that you can build a strong cybersecurity posture.”
The elements of such an approach include the establishment of formal security frameworks; regular reviews and updates to risk management plans to keep up with the threat landscape; and expanding the defense toolkit where necessary to combat high-level threats, Yang explains. “New technologies such as AI and machine learning need to be correctly applied to shore up defenses.”
In a hybrid work environment, enterprises also have to acknowledge they may need to cede more control over security than they used to. “We still see security frameworks and models based on the idea that you will have a network located entirely within a physical office building, and all of the laptops are going to be Windows laptops, and they're going to be managed by your company's staff,” says Ryan. “Some people live in that world. But increasingly many of us don't.”

"Devices, cloud, identity – those are the new points where organizations need to build guardrails.”
Robin Doherty
Principal Consultant, Global Head of BISOs & Business Information Security Officer (BISO), APAC, Thoughtworks
“Historically, people thought the network perimeter was the only place you needed to apply security controls,” agrees Doherty. “But now that's not sufficient because a lot of what we do as businesses is in the cloud or on people's devices that are not necessarily on the network. Devices, cloud, identity – those are the new points where organizations need to build guardrails.”
This makes investing in the team’s ability to understand and detect security problems and risks doubly important. Doherty advocates embracing offensive security – that is, actually simulating cyber incidents and attacks – to get the most accurate picture of the enterprise’s defenses and weak spots.
“There's a maxim in security that it's a lot easier to be an attacker than a defender, because as a defender, you have to plug thousands of gaps – but as an attacker, you only have to find one,” he says. “If you just keep buying tools and plugging them in with the thinking that they work well enough, you’re probably going to have gaps. But if you pay people to specifically figure out how to attack your organization, they will find the holes in those configurations for you.”
Threat modeling – taking the time to map out the risks that the organization may face, evaluating their likelihood and potential impact; and deciding where controls are best allocated accordingly – is another valuable exercise.
“Organizations can look at it as a Swiss cheese model for risk,” Doherty explains. “If you have one big piece of cheese with lots of holes in it, attackers only need to find one hole. If you have many layers of cheese, they need to find the holes in each. What that means is don't invest in one place. Create layers.”
The Swiss cheese security model
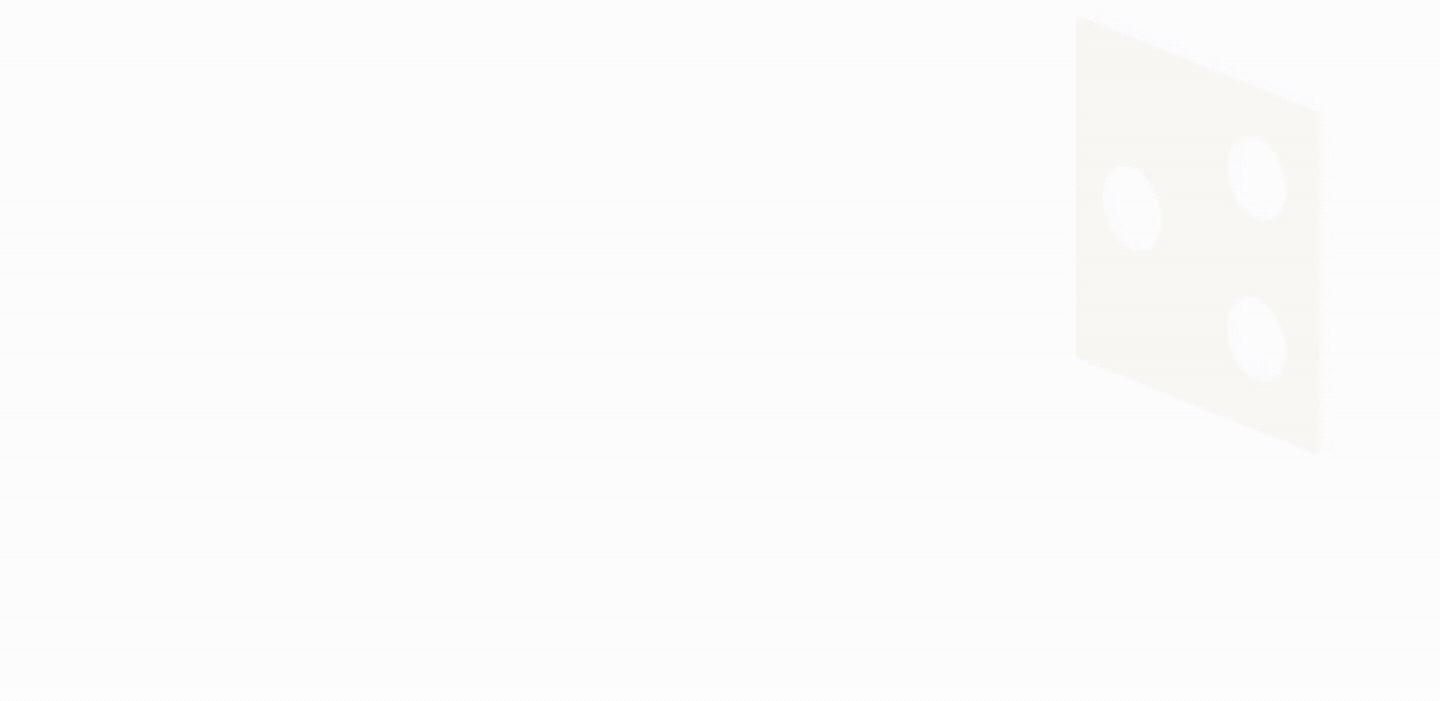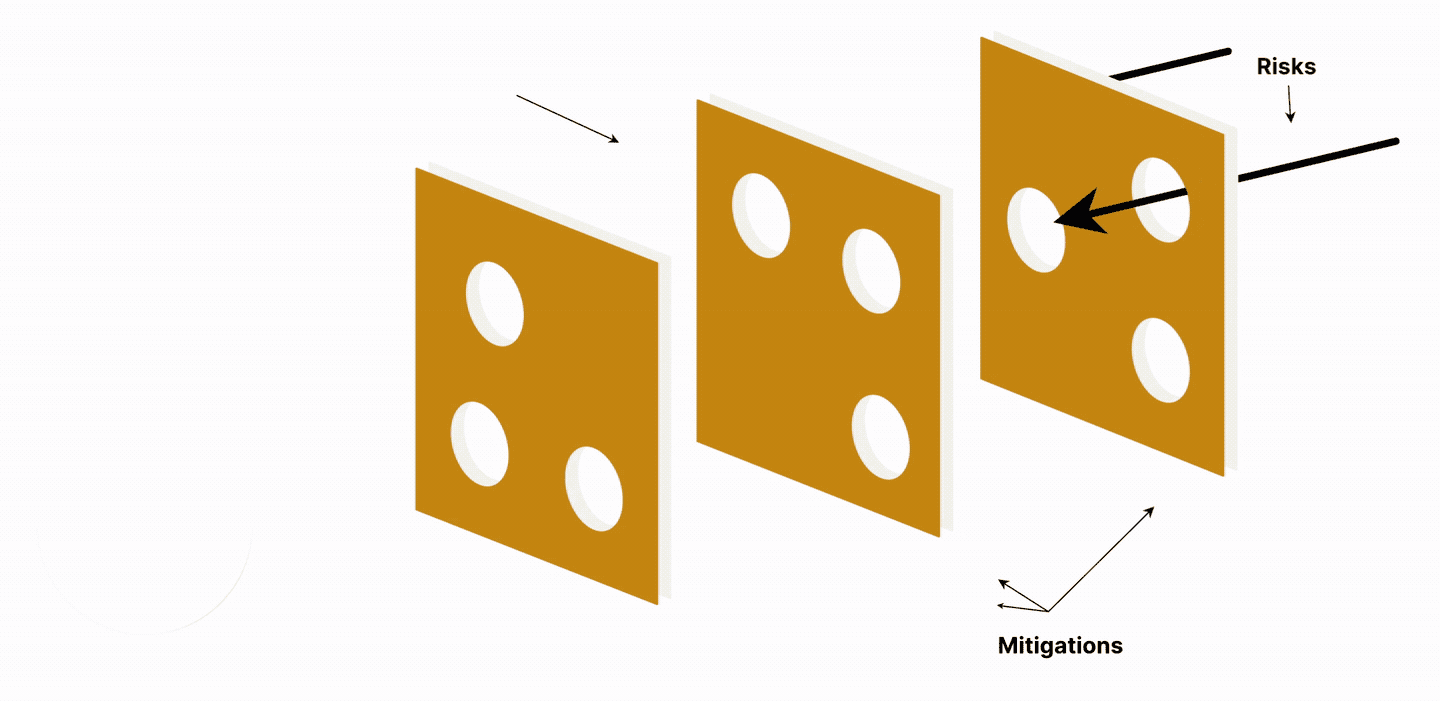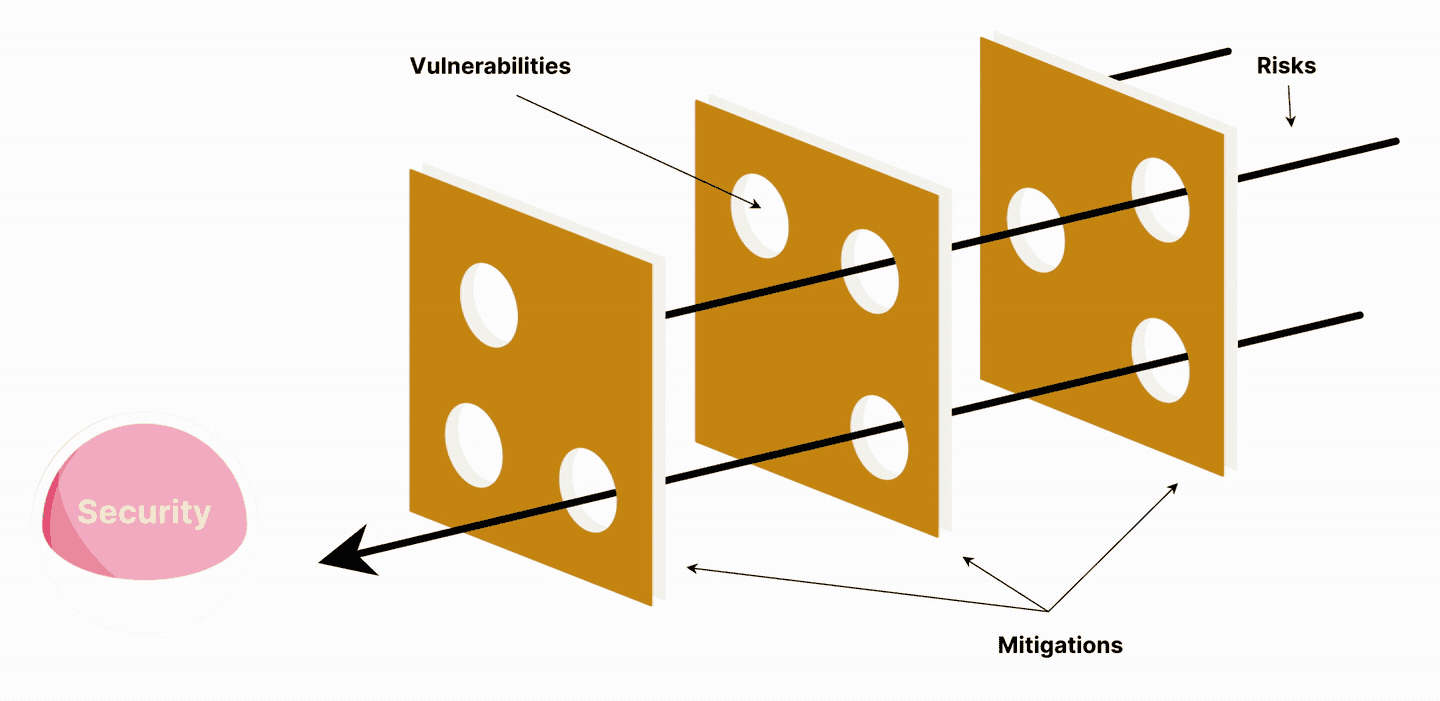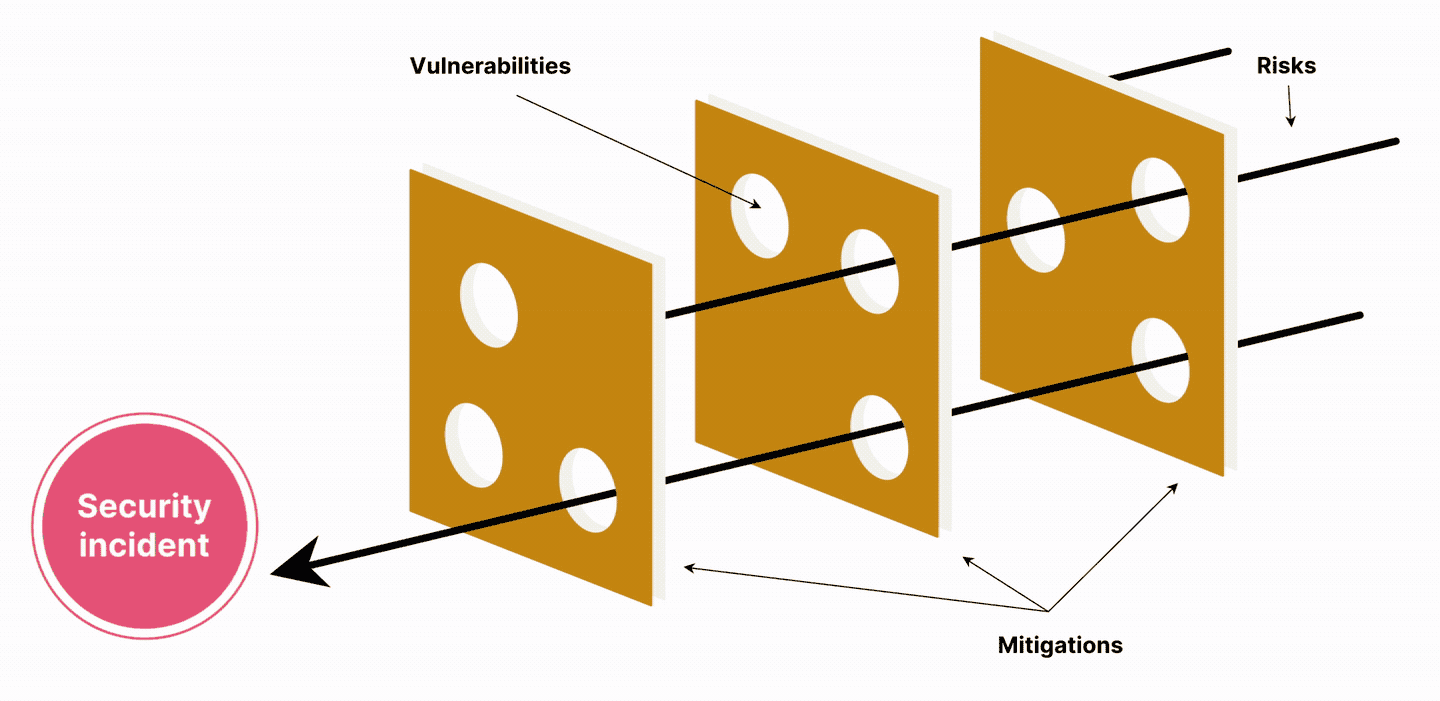

Working through security challenges in a structured way can ensure priorities are set and resources channeled wisely.
“The most important thing is to make sensible decisions about what information you have, where you want it to be, and how that matches with the realities of people working wherever they are and with third parties that you may not have the greatest visibility over,” says Ryan. “Then instead of throwing money at something very shiny, figuring out the minimum practical things for you to be doing, because there are certainly going to be lots of solutions out there.”
When assessing an enterprise’s weak spots, security teams often zero in on the people – but according to Doherty it’s rare that incidents are driven by the human factor alone. “When you look for what went wrong, it's usually quite easy to find a mistake made by a person; it's a bit harder to analyze that mistake and figure out what caused it,” he says. “It’s usually not just a person waking up one day and deciding to make a mistake; it's normally the system around them that guides them to that mistake. Or at least a combination of the two.”
He urges business leaders to take a page from health and safety culture. “One example is road traffic design,” Doherty explains. “If you have a car full of rowdy passengers and a distracted driver who runs into a concrete post on the side of the road, you could easily write it off as a tragic result of human error and believe there's nothing that can be done from a road administrator's point of view. But if you think about it critically, you should acknowledge that people make mistakes when they're under pressure or distracted, which are very normal problems in IT and security as well. So maybe you remove the concrete posts from the side of the road, rather than expecting every driver to be perfect.”
In other words, design choices and deliberate decision-making can do more to embed security than most tech tools. Data is a case in point. As so many intrusions and issues are focused on data, the first priority should be to reassess what kind of data the company is gathering and is therefore forced to protect.
“Identity information is where many data breaches occur, and we know we can't stop those from happening 100% of the time, but you can curb their impact by limiting the amount of data that can be stolen in the first place,” says Ryan. “It’s easy to just gather as much data as you can, because it contains a lot of insights if you ask the right questions. But it’s very important to revisit questions around the data that you’re gathering, to make sure you understand why it's important, and whether you really need it.”

“It’s easy to just gather as much data as you can, because it contains a lot of insights if you ask the right questions. But it’s very important to revisit questions around the data that you’re gathering, to make sure you understand why it's important, and whether you really need it.”
Lilly Ryan
Global Secure Delivery Strategy Lead, Thoughtworks
“Practice data minimization,” agrees Doherty. “Don't collect information if you don't need it, and delete it when you don't need it anymore.”
Organizations can also reduce risk by learning to think in terms of ‘supply chain’ rather than ‘enterprise’ security, choosing the partners they work with carefully and capping the number where possible.
“More than ever there’s a number of different parties involved in any given piece of software or service we might be using, or building,” Ryan points out. “It can be really hard to trace that all the way back to find out where something has gone wrong, or feel certain that you’ve got control from beginning to end.”
Supply chain risk is also increasing as AI capabilities are bundled into commonly used solutions like Microsoft 365 that can give employees access without the executives who ‘control’ security even being aware, Ryan points out.
However, rather than looking to ban or completely eliminate the use of such tools, business leaders “should accept that some things are out of the company’s control, and provide a ‘paved road’ to encourage teams to use tools in the right way,” she says.
Part of that ‘paved road’ is a clear security policy, which Thoughtworks experts recommend even the smallest enterprise set out – and refresh regularly.
“It's not just about having the words written on a piece of paper,” says Doherty. “The more important thing is that the organization is following the practices in the policy, adapting and evolving them, and documenting that continuously.”
“The approach that Thoughtworks has taken is explicitly governing,” he adds. “Having an industry standard framework that you assess yourself against regularly, or getting an external company to do it. Whichever approach you take, you should get recommendations to continually evolve and improve the security framework that you're using.”
iii. Fostering a security mindset and culture
As the boundaries of the enterprise and the threat landscape change, adoption and implementation of security policies have become a more enterprise-wide responsibility than they might have been in past. As Yang puts it: “Shifting tech and business practices such as longer data processing times, and the growing adoption of cloud, remote work and automation, mean modern security practices have evolved from being the primary domain of security teams to an organizational effort.”

"The growing adoption of cloud, remote work and automation, mean modern security practices have evolved from being the primary domain of security teams to an organizational effort.”
Lu Yang
Head of Incubator Service Line Security, Thoughtworks
This means that while the function may rest primarily with a security or IT team, protecting the organization is a collective responsibility.
“It's crucial to look at the root causes and collaborate more with other departments, focusing on the business perspective,” says Yang. “Forming functional working groups across the organization is an effective way to implement and execute the organization’s cybersecurity strategy. Importantly, establishing a feedback mechanism allows identified needs to be incorporated into ongoing security management to create a more comprehensive security posture.”
The security feedback loop


Diversity of views and experience can also make direct contributions to an enterprise’s resilience. “When we're building software, and we're looking at threat modeling, we want to make sure we have at least one representative from each major group of stakeholders because there are always going to be needs that somebody has that you didn't anticipate,” Ryan explains. “Getting different perspectives also means someone will realize: ‘Oh, actually, every second Thursday, the cleaners come in and they also have a set of keys to the office’ – a vulnerability you’ve never considered. You don't want to make the room so crowded that nobody can have a conversation. But you need to take a holistic view.”
“People in security tend to come from risk management, accountancy, or technology but there are much fewer people with non-standard or unusual backgrounds in the realm, who can bring new ways of looking at these very complex problems,” agrees Doherty.
Strong executive sponsorship helps rally this diverse group of stakeholders and underlines that security is a priority. “One of the things we advocate is business leaders taking ownership of security and integrating it into their strategies, rather than it being relegated to a purely tech problem,” Doherty says. “There should always be a board member or an executive with an idea about what the organization should invest in.”
Training for business leaders can help build this capability, since many executives will lack formal security experience.
“Directors and executives are paying more attention than they used to, but they're also approaching these topics from a low base of existing knowledge, so keeping them informed on the latest developments in cybersecurity practices is really important,” says Doherty. “It’s also critical that the information that is presented to them is accessible and useful. When people come to you with ideas, whether salespeople or senior executives, you need to be able to prioritize needs over the fads. And that relies on having that understanding of the threat model, the strategy and where you're heading.”
Yang recommends appointing a chief information security officer (CISO) to lead the organization’s cybersecurity strategy and oversee its implementation in close coordination with the IT and risk leadership. “At the highest levels of the organization, there needs to be maximum support and commitment and that includes allocating resources to cybersecurity,” he says. “Traditionally, the security department operated in its own lane, but nowadays it's all about teamwork.”
Beyond the management tier, embedding ‘security champions’ throughout the enterprise can pave the way for policies and practices to be integrated at the day-to-day level.
“We have a program where we identify people on product or delivery teams who take some ownership for security,” says Doherty. “As they’re not security experts, or generally didn’t start off that way, they get training, and get connected to a community of their peers, and to the security team. They become a way of assuring the organization that necessary security controls are being integrated into the products that they're building.”
Moving from security policies to a security culture also requires honesty and transparency – as well as a degree of bravery, Ryan notes.

“Security requires a space to ask hard questions, especially where the answers might not be very clear cut. It requires us to imagine the worst case scenario, and that's not always comfortable."
Lilly Ryan
Global Secure Delivery Strategy Lead, Thoughtworks
“Security requires a space to ask hard questions, especially where the answers might not be very clear cut,” she explains. “It requires us to imagine the worst case scenario, and that's not always comfortable. But it does mean that if we spend the time to anticipate some of those issues, and think about the impacts and their context and our needs as a business, we're going to come up with answers that meet those needs, and enable us to make decisions that are aligned with them – rather than just picking solutions up off the shelf.”
Doherty also urges enterprises to break down some of the fears and misconceptions around security as a topic. “To ensure buy-in and participation from throughout the organization, the first thing you can do is make it fun,” he says. “People expect security to be boring so anything that's a step up from a 50-page document they have to read as part of an onboarding is an improvement. At Thoughtworks we've run weeklong cybersecurity awareness and capability campaigns centered around the idea of defense in depth, and made a mascot for that – a blue-ringed octopus.”
“The other thing is to make security professionally interesting,” Doherty adds. “When we have security champions on a team, we make clear this is a benefit to the individual. By getting involved and learning about security, you’re making yourself more valuable to future employers because this is a capability that most organizations are lacking.”
Taking smaller security incidents as a learning experience that allows the team to test out incident response plans can also help build skills and readiness for larger events – and remove some of the fear around them.
“You have to prepare for the breadth of reality and the fact that things will go wrong," says Ryan. “Doing a bit of thinking and practicing ahead of time should help make incidents less scary if they happen – because sometimes they do.”
iv. Embedding readiness and resilience
Though incidents and more sophisticated threats may be almost inevitable, Thoughtworks experts counsel enterprises not to succumb to negativity about the security outlook.
As Doherty puts it: “There’s a never-ending stream of stories in the media about the next big security breach – but that stream of bad news is not really unexpected. It's often the end result of some of the actions taken or not taken in the past.”
“While there’s a lot of apprehension, even panic about security at the moment, in a sense it’s positive that it’s become a bigger issue as it’s approaching a tipping point,” Ryan points out. “More people and organizations have direct experience with things like data breaches and are improving their practices as a result, because they’re personally invested in making change.”
“The market is the driving force behind government and private sector investments,” Doherty agrees. “Overall concern for security has increased among the general public, which drives government action and organizations’ investment into boosting cybersecurity and these are positive developments overall.”
Research shows both governments and enterprises devoting more resources to the cybersecurity struggle, with spending to climb 14% in 2024 alone, led by growth in the cloud security and data privacy segments, according to Gartner.
Global investment in security surges
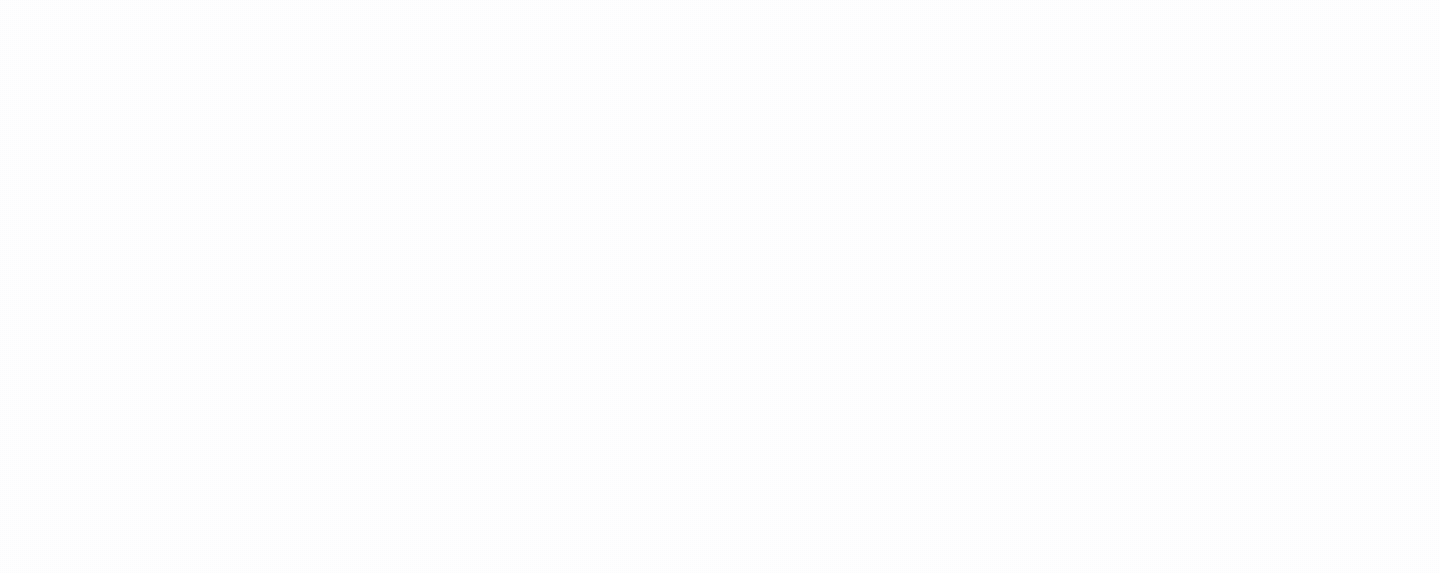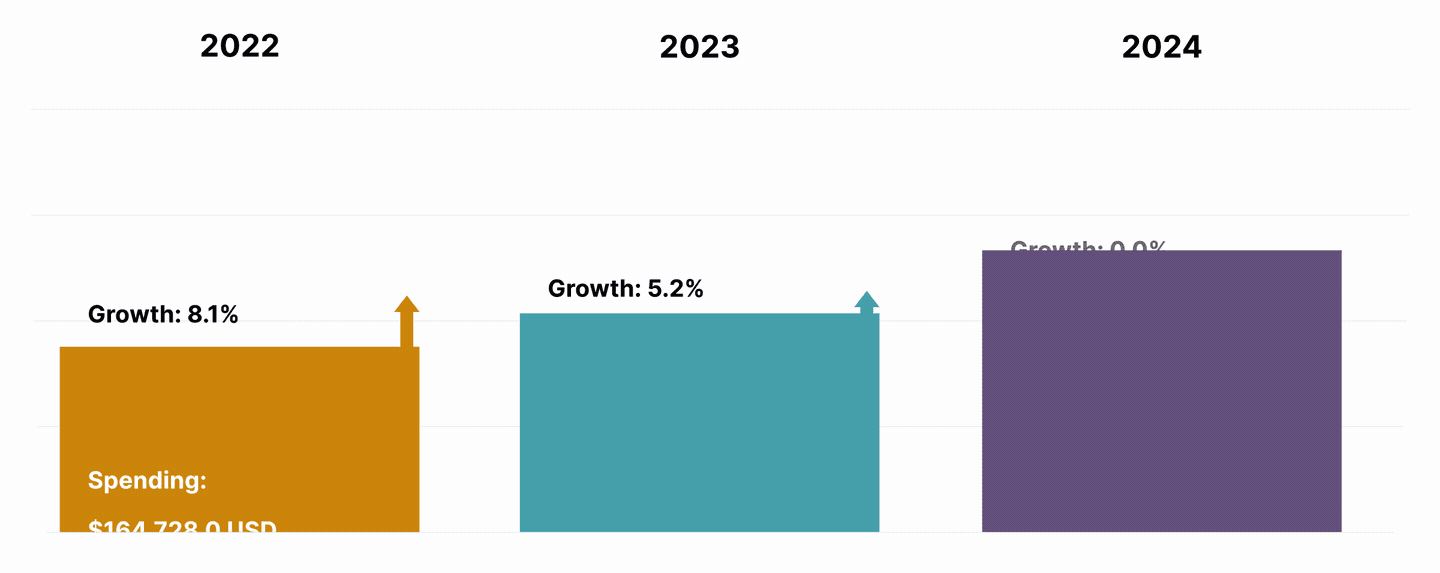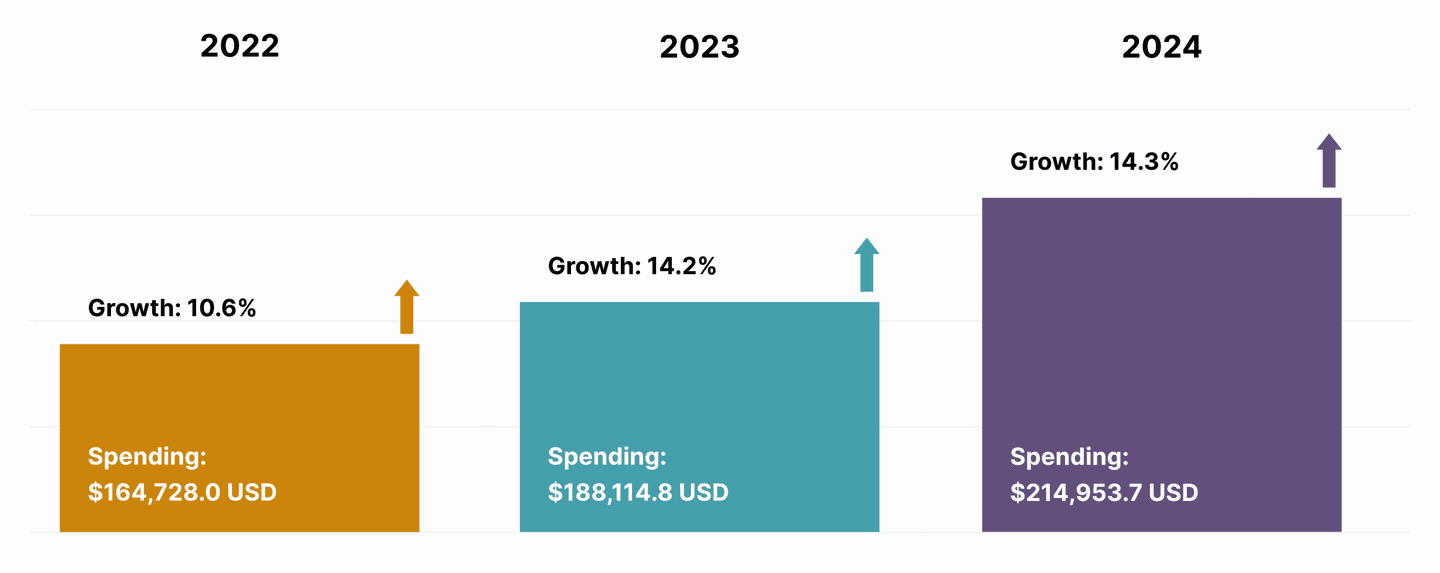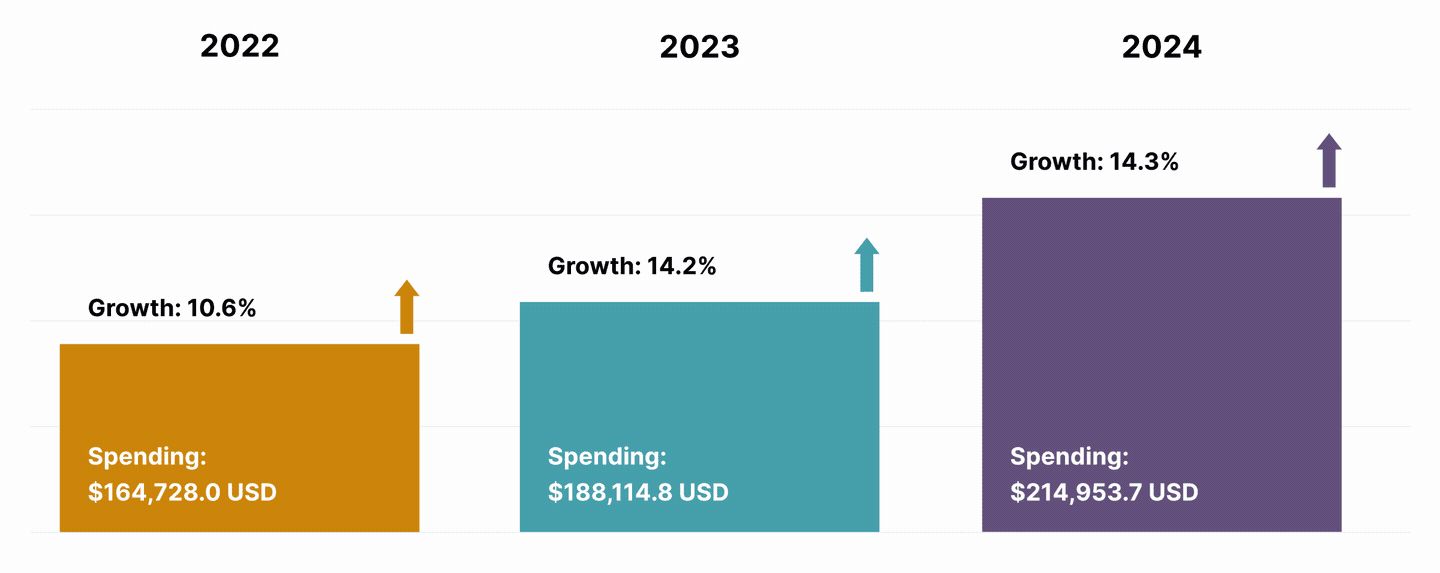

However, even as investments grow, “the challenge is getting the balance right,” says Doherty, managing resources carefully while not neglecting the need to develop security culture and practices.
“You want to be investing enough to keep the risk within your tolerance threshold, but not any more than that. If you're not increasing your security investment, then you're probably not keeping pace with the change that's occurring in the threat landscape. Unfortunately, a lot of organizations are probably being outpaced at the moment because the state of the economy over the last few years has resulted in them having less to invest.”
Even in a tougher economic environment, Yang advises enterprises to keep a close eye on developments in both the threat landscape and security solutions, as being proactive about security brings a number of rewards.
“It’s extremely important to use all the tools at our disposal to solve vulnerability problems,” he says. “By doing that, organizations can create more flexible systems, protect their sensitive data and cultivate a culture of trust and openness. That not only reduces risk, but also strengthens relationships with key stakeholders, to ensure long-term success.”

“It’s extremely important to use all the tools at our disposal to solve vulnerability problems. By doing that, organizations can create more flexible systems, protect their sensitive data and cultivate a culture of trust and openness. That not only reduces risk, but also strengthens relationships with key stakeholders, to ensure long-term success.”
Lu Yang
Head of Incubator Service Line Security, Thoughtworks
About the contributors

Robin Doherty
Principal Consultant, Global Head of BISOs & Business Information Security Officer (BISO), APAC, Thoughtworks

Lilly Ryan
Global Secure Delivery Strategy Lead, Thoughtworks

Lu Yang
Head of Incubator Service Line Security, Thoughtworks
Perspectives delivered to your inbox
Timely business and industry insights for digital leaders.
The Perspectives subscription brings you our experts’ best podcasts, articles, videos and events to expand upon our popular Perspectives publication.
















